ptcpdump: 可捕获进程、容器或 Pod 的增强型tcpdump抓包
ptcpdump 介绍
ptcpdump 是一个命令行工具,用于监控和分析网络通信数据包。它是 Linux 和 Unix 系统上的一个常用工具。以下是 ptcpdump 的一些主要特点和用途:
- 数据包捕获:能够捕获网络接口上的数据包,支持多种网络协议,如 TCP、UDP、ICMP 等。
- 数据包分析:可以解析数据包的内容,显示各层协议的详细信息,如源/目的 IP 地址、端口号、数据负载等。
- 过滤选项:提供丰富的过滤选项,可以按照协议类型、源/目的地址、端口号等条件过滤感兴趣的数据包。
- 实时显示:可以实时显示捕获的数据包,并支持滚动显示新数据包。
- 输出格式化:支持多种输出格式,如常见的描述性格式、Hex 转储格式、JSON 格式等。
- 保存数据包:可以将捕获的数据包保存到文件,供后续分析使用。
- 网络故障诊断:通过观察网络数据包可以帮助诊断网络故障,如连接问题、性能问题等。
- 安全监控:可以用于监测可疑的网络活动,辅助安全分析和入侵检测。
ptcpdump 是一个使用 eBPF 技术开发的、类 tcpdump 的网络抓包工具。 它除了兼容 tcpdump 的常用命令行参数以及包过滤语法外,还额外提供了如下核心特性:
- 在输出中记录和显示发送网络流量的进程、容器、Pod 信息。
- 支持对指定进程、容器以及 Pod 进行抓包。
- 支持将抓取的数据包保存为 pcapng 格式,可以使用 tcpdump 或者 Wireshark 做进一步分析。
- 当在 Wireshark 中打开保存的 pcapng 文件时,将能够看到每个数据包对应的进程、容器、Pod 信息。
- 使用静态链接的方式编译该工具,系统中不需要安装额外的系统链接库。
更多信息请参考项目的源代码仓库:https://github.com/mozillazg/ptcpdump
总的来说,ptcpdump 是一个强大的网络分析工具,广泛应用于网络故障排查、性能监控、安全审计等领域。对于网络管理员和开发者来说,掌握使用 ptcpdump 是非常有价值的技能。
要求
Linux 内核版本 >= 5.2
我使用rocky liunx 8也正常使用
[root@localhost tmp]# uname -r 4.18.0-553.el8_10.x86_64
用法
示例命令
像 tcpdump 这样的过滤器:
sudo ptcpdump -i eth0 tcp
sudo ptcpdump -i eth0 tcp and port 80 and host 10.10.1.1
sudo ptcpdump -i eth0 'tcp[tcpflags] & (tcp-syn|tcp-fin) != 0'
多种接口:
sudo ptcpdump -i eth0 -i lo
按进程筛选:
sudo ptcpdump -i any --pid 1234
sudo ptcpdump -i any --pname curl
通过运行目标程序按进程捕获:
sudo ptcpdump -i any -- curl ubuntu.com
按容器筛选:
sudo ptcpdump -i any --container-id 36f0310403b1
sudo ptcpdump -i any --container-name test
按 Pod 筛选:
sudo ptcpdump -i any --pod-name test.default
以 PcapNG 格式保存数据:
sudo ptcpdump -i any -w demo.pcapng
sudo ptcpdump -i any -w - port 80 | tcpdump -n -r -
sudo ptcpdump -i any -w - port 80 | tshark -r -
输出中网络流量的进程、容器和 Pod 信息
默认情况下,ptcpdump 将在输出中显示简单的进程信息
[root@k145 tmp]# ./ptcpdump -i any -c 4 port 80 or port 443
2024-08-13 09:31:27 WARN skip Docker Engine integration due to Cannot connect to the Docker daemon at unix:///var/run/docker.sock. Is the docker daemon running?
2024-08-13 09:31:29 WARN skip containerd integration due to failed to dial "/run/containerd/containerd.sock": context deadline exceeded
2024-08-13 09:31:29 WARN skip kubernetes integration due to [connect using endpoint /var/run/dockershim.sock: no such file or directory, connect using endpoint /var/run/cri-dockerd.sock: no such file or directory, connect using endpoint /run/crio/crio.sock: no such file or directory, connect using endpoint /run/containerd/containerd.sock: no such file or directory]
2024-08-13 09:31:29 WARN skip attach cgroup due to get cgroup v2 root dir failed: cgroupv2 is not mounted
2024-08-13 09:31:30 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-08-13 09:31:30 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
09:31:34.548919 cali6e0cd4328a0 nginx-ingress-controller.896164 In IP 10.42.2.238.55082 > 10.43.0.1.443: Flags [P.], seq 3680874937:3680874976, ack 3350507407, win 5838, length 39, ParentProc [catatonit.896152]
09:31:34.553200 cali6e0cd4328a0 nginx-ingress-controller.896164 Out IP 10.43.0.1.443 > 10.42.2.238.55082: Flags [P.], seq 3350507407:3350507497, ack 3680874976, win 9865, length 90, ParentProc [catatonit.896152]
09:31:34.553251 cali6e0cd4328a0 nginx-ingress-controller.896164 Out IP 10.43.0.1.443 > 10.42.2.238.55082: Flags [P.], seq 3350507497:3350508275, ack 3680874976, win 9865, length 778, ParentProc [catatonit.896152]
09:31:34.553298 cali6e0cd4328a0 nginx-ingress-controller.896164 In IP 10.42.2.238.55082 > 10.43.0.1.443: Flags [.], seq 3680874976, ack 3350507497, win 5838, length 0, ParentProc [catatonit.896152]
4 packets captured
5 packets received by filter
0 packets dropped by kernel
通过 -v 参数,查看更详细的进程、容器以及 Pod 信息:
[root@k145 tmp]# ./ptcpdump -i any -c 4 -v port 80 or port 443
2024-08-13 09:32:10 WARN skip Docker Engine integration due to Cannot connect to the Docker daemon at unix:///var/run/docker.sock. Is the docker daemon running?
2024-08-13 09:32:12 WARN skip containerd integration due to failed to dial "/run/containerd/containerd.sock": context deadline exceeded
2024-08-13 09:32:12 WARN skip kubernetes integration due to [connect using endpoint /var/run/dockershim.sock: no such file or directory, connect using endpoint /var/run/cri-dockerd.sock: no such file or directory, connect using endpoint /run/crio/crio.sock: no such file or directory, connect using endpoint /run/containerd/containerd.sock: no such file or directory]
2024-08-13 09:32:12 WARN skip attach cgroup due to get cgroup v2 root dir failed: cgroupv2 is not mounted
2024-08-13 09:32:12 WARN ptcpdump: capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
09:32:13.340500 cali6e0cd4328a0 Out IP (tos 0x0, ttl 63, id 59610, offset 0, flags [DF], proto TCP (6), length 273)
10.43.0.1.443 > 10.42.2.238.55082: Flags [P.], cksum 0x23db, seq 3350512044:3350512265, ack 3680875273, win 9865, options [nop,nop,TS val 912664807 ecr 964018093], length 221
09:32:13.340637 cali6e0cd4328a0 In IP (tos 0x0, ttl 64, id 22917, offset 0, flags [DF], proto TCP (6), length 52)
10.42.2.238.55082 > 10.43.0.1.443: Flags [.], cksum 0x176a, seq 3680875273, ack 3350512265, win 5837, options [nop,nop,TS val 964021840 ecr 912664807], length 0
09:32:17.171670 cali6e0cd4328a0 In IP (tos 0x0, ttl 64, id 22918, offset 0, flags [DF], proto TCP (6), length 91)
10.42.2.238.55082 > 10.43.0.1.443: Flags [P.], cksum 0x1791, seq 3680875273:3680875312, ack 3350512265, win 5838, options [nop,nop,TS val 964023755 ecr 912664807], length 39
Process (pid 896164, cmd /nginx-ingress-controller, args /nginx-ingress-controller --election-id=rke2-ingress-nginx-leader --controller-class=k8s.io/ingress-nginx --ingress-class=nginx --configmap=kube-system/rke2-ingress-nginx-controller --validating-webhook=:8443 --validating-webhook-certificate=/usr/local/certificates/cert --validating-webhook-key=/usr/local/certificates/key --watch-ingress-without-class=true)
ParentProc (pid 896152, cmd /usr/bin/catatonit, args /usr/bin/catatonit -- /nginx-ingress-controller --election-id=rke2-ingress-nginx-leader --controller-class=k8s.io/ingress-nginx --ingress-class=nginx --configmap=kube-system/rke2-ingress-nginx-controller --validating-webhook=:8443 --validating-webhook-certificate=/usr/local/certificates/cert --validating-webhook-key=/usr/local/certificates/key --watch-ingress-without-class=true)
09:32:17.178764 cali6e0cd4328a0 Out IP (tos 0x0, ttl 63, id 59611, offset 0, flags [DF], proto TCP (6), length 142)
10.43.0.1.443 > 10.42.2.238.55082: Flags [P.], cksum 0xe788, seq 3350512265:3350512355, ack 3680875312, win 9865, options [nop,nop,TS val 912666726 ecr 964023755], length 90
Process (pid 896164, cmd /nginx-ingress-controller, args /nginx-ingress-controller --election-id=rke2-ingress-nginx-leader --controller-class=k8s.io/ingress-nginx --ingress-class=nginx --configmap=kube-system/rke2-ingress-nginx-controller --validating-webhook=:8443 --validating-webhook-certificate=/usr/local/certificates/cert --validating-webhook-key=/usr/local/certificates/key --watch-ingress-without-class=true)
ParentProc (pid 896152, cmd /usr/bin/catatonit, args /usr/bin/catatonit -- /nginx-ingress-controller --election-id=rke2-ingress-nginx-leader --controller-class=k8s.io/ingress-nginx --ingress-class=nginx --configmap=kube-system/rke2-ingress-nginx-controller --validating-webhook=:8443 --validating-webhook-certificate=/usr/local/certificates/cert --validating-webhook-key=/usr/local/certificates/key --watch-ingress-without-class=true)
4 packets captured
7 packets received by filter
0 packets dropped by kernel
支持对指定进程、容器或 Pod 进行抓包
指定进程 pid 抓包
可以通过 --pid 参数指定要抓包的进程 pid,实现对指定进程进行抓包:
[root@k145 tmp]# ptcpdump -i any -c 4 --pid 82106
2024-07-07 13:11:40 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-07-07 13:11:40 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:11:50.170538 ens33 python3.10.82106 Out IP 10.0.2.15.36648 > 13.251.96.10.443: Flags [S], seq 1633417447, win 64240, length 0
13:11:50.369972 ens33 python3.10.82106 In IP 13.251.96.10.443 > 10.0.2.15.36648: Flags [S.], seq 1793291274, ack 1633417448, win 64240, length 0
2 packets captured
3 packets received by filter
0 packets dropped by kernel
指定进程名称抓包
可以通过 --pname 参数指定进程名称(comm),实现指定进程名称抓包:
[root@k145 tmp]# ptcpdump -i any -c 2 --pname curl
2024-07-07 13:23:18 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-07-07 13:23:18 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:23:24.881499 lo curl.26511 Out IP 127.0.0.1.43332 > 127.0.0.53.53: 44133+ [1au] A? mozillazg.com. (42)
13:23:24.881663 lo curl.26511 Out IP 127.0.0.1.43332 > 127.0.0.53.53: 14694+ [1au] AAAA? mozillazg.com. (42)
2 packets captured
2 packets received by filter
0 packets dropped by kernel
通过运行目标程序来抓包
有需要的话,也可以通过使用 -- 参数运行目标程序的方式来实现对特定程序进行抓包:
[root@localhost tmp]# ./ptcpdump -i any -- curl -I https://199604.com
2024-08-13 10:06:46 WARN skip Docker Engine integration due to Cannot connect to the Docker daemon at unix:///var/run/docker.sock. Is the docker daemon running?
2024-08-13 10:06:47 WARN skip attach cgroup due to get cgroup v2 root dir failed: cgroupv2 is not mounted
2024-08-13 10:06:48 WARN the kernel does not support netfilter based NAT feature, skip attach kprobe/nf_nat_packet
2024-08-13 10:06:48 WARN the kernel does not support netfilter based NAT feature, skip attach kprobe/nf_nat_manip_pkt
2024-08-13 10:06:48 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-08-13 10:06:48 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10:06:48.323852 ens33 curl.2001 Out IP 192.168.100.135.38965 > 8.8.8.8.53: 19030+ A? 199604.com. (28), ParentProc [ptcpdump.1991]
10:06:48.324064 ens33 curl.2001 Out IP 192.168.100.135.38965 > 8.8.8.8.53: 54103+ AAAA? 199604.com. (28), ParentProc [ptcpdump.1991]
10:06:58.335129 ens33 curl.2001 Out IP 192.168.100.135.41500 > 114.114.114.114.53: 19030+ A? 199604.com. (28), ParentProc [ptcpdump.1991]
10:06:58.335910 ens33 curl.2001 Out IP 192.168.100.135.41500 > 114.114.114.114.53: 54103+ AAAA? 199604.com. (28), ParentProc [ptcpdump.1991]
10:06:58.472980 ens33 curl.2001 In IP 114.114.114.114.53 > 192.168.100.135.41500: 19030 1/0/0 A 47.106.219.217 (44), ParentProc [ptcpdump.1991]
10:06:58.577895 ens33 curl.2001 In IP 114.114.114.114.53 > 192.168.100.135.41500: 54103 0/1/0 (102), ParentProc [ptcpdump.1991]
10:06:58.887627 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [S], seq 811975402, win 29200, length 0, ParentProc [ptcpdump.1991]
10:06:58.906804 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [S.], seq 526528615, ack 811975403, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:58.909192 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [.], seq 811975403, ack 526528616, win 29200, length 0, ParentProc [ptcpdump.1991]
10:06:58.984973 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811975403:811975920, ack 526528616, win 29200, length 517, ParentProc [ptcpdump.1991]
10:06:58.985565 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526528616, ack 811975920, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.004617 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [P.], seq 526528616:526530881, ack 811975920, win 64240, length 2265, ParentProc [ptcpdump.1991]
10:06:59.004938 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [.], seq 811975920, ack 526530881, win 33580, length 0, ParentProc [ptcpdump.1991]
10:06:59.012610 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811975920:811976005, ack 526530881, win 33580, length 85, ParentProc [ptcpdump.1991]
10:06:59.013655 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530881, ack 811976005, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.030576 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [P.], seq 526530881:526530985, ack 811976005, win 64240, length 104, ParentProc [ptcpdump.1991]
10:06:59.032378 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976005:811976050, ack 526530985, win 33580, length 45, ParentProc [ptcpdump.1991]
10:06:59.033524 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530985, ack 811976050, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.033617 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530985, ack 811976098, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.033661 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530985, ack 811976132, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.033825 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530985, ack 811976194, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.033870 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976194:811976224, ack 526530985, win 33580, length 30, ParentProc [ptcpdump.1991]
10:06:59.034098 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526530985, ack 811976224, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.033651 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976050:811976098, ack 526530985, win 33580, length 48, ParentProc [ptcpdump.1991]
10:06:59.033719 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976098:811976132, ack 526530985, win 33580, length 34, ParentProc [ptcpdump.1991]
10:06:59.033858 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976132:811976194, ack 526530985, win 33580, length 62, ParentProc [ptcpdump.1991]
10:06:59.155399 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [P.], seq 526530985:526531015, ack 811976224, win 64240, length 30, ParentProc [ptcpdump.1991]
10:06:59.236007 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [.], seq 811976224, ack 526531015, win 33580, length 0, ParentProc [ptcpdump.1991]
HTTP/2 200
server: openresty
date: Tue, 13 Aug 2024 02:06:53 GMT
content-type: text/html; charset=UTF-8
10:06:59.279560 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [P.], seq 526531015:526531371, ack 811976224, win 64240, length 356, ParentProc [ptcpdump.1991]
vary: Accept-Encoding
x-powered-by: PHP/8.0.30
set-cookie: wp-editormd-lang=zh-CN; path=/
link: <https://199604.com/wp-json/>; rel="https://api.w.org/"
10:06:59.279779 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [.], seq 811976224, ack 526531371, win 36500, length 0, ParentProc [ptcpdump.1991]
link: <https://199604.com/wp-json/wp/v2/pages/2535>; rel="alternate"; type="application/json"
link: <https://199604.com/>; rel=shortlink
vary: Accept-Encoding
strict-transport-security: max-age=31536000
10:06:59.282568 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526531371, ack 811976247, win 64240, length 0, ParentProc [ptcpdump.1991]
10:06:59.281905 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [P.], seq 811976224:811976247, ack 526531371, win 36500, length 23, ParentProc [ptcpdump.1991]
10:06:59.284945 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [F.], seq 811976247, ack 526531371, win 36500, length 0, ParentProc [ptcpdump.1991]
10:06:59.286053 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [.], seq 526531371, ack 811976248, win 64239, length 0, ParentProc [ptcpdump.1991]
10:06:59.299490 ens33 curl.2001 In IP 47.106.219.217.443 > 192.168.100.135.49454: Flags [FP.], seq 526531371, ack 811976248, win 64239, length 0, ParentProc [ptcpdump.1991]
10:06:59.299652 ens33 curl.2001 Out IP 192.168.100.135.49454 > 47.106.219.217.443: Flags [.], seq 811976248, ack 526531372, win 36500, length 0, ParentProc [ptcpdump.1991]
36 packets captured
36 packets received by filter
0 packets dropped by kernel
指定容器抓包
可以通过 --container-id 参数指定容器 id 进行抓包:
[root@localhost tmp]# ptcpdump -i any -c 2 --container-id 36f0310403b1
2024-07-07 13:36:19 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-07-07 13:36:19 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:36:24.191242 veth09dec8f curl.32636 In IP 172.19.0.2.48960 > 18.139.194.139.443: Flags [S], seq 3213779351, win 64240, length 0, Container [kind-control-plane]
13:36:24.191369 wlp4s0 curl.32636 Out IP 192.168.1.50.48960 > 18.139.194.139.443: Flags [S], seq 3213779351, win 64240, length 0, Container [kind-control-plane]
2 packets captured
2 packets received by filter
0 packets dropped by kernel
也可以通过 --container-name 参数指定容器名称进行抓包:
[root@localhost tmp]# ptcpdump -i any -c 2 --container-name kind-control-plane
2024-07-07 13:37:16 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-07-07 13:37:16 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:37:22.560764 veth09dec8f curl.33093 In IP 172.19.0.2.39084 > 18.139.194.139.443: Flags [S], seq 3645727033, win 64240, length 0, Container [kind-control-plane]
13:37:22.561010 wlp4s0 curl.33093 Out IP 192.168.1.50.39084 > 18.139.194.139.443: Flags [S], seq 3645727033, win 64240, length 0, Container [kind-control-plane]
2 packets captured
2 packets received by filter
0 packets dropped by kernel
指定 Pod 抓包
可以通过 --pod-name 参数指定 Pod 名称进行抓包, 参数值的格式为 <pod 名称>.<pod 命名空间>:
[root@localhost tmp]# ptcpdump -i any -c 2 --pod-name test.default
2024-07-07 13:38:29 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output
2024-07-07 13:38:29 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:38:34.175752 eth0 wget.33660 Out IP 172.19.0.2.51564 > 13.215.144.61.443: Flags [S], seq 567383917, win 64240, length 0, Container [test], Pod [test.default]
13:38:34.372894 eth0 wget.33660 In IP 13.215.144.61.443 > 172.19.0.2.51564: Flags [S.], seq 2654865684, ack 567383918, win 65084, length 0, Container [test], Pod [test.default]
2 packets captured
3 packets received by filter
0 packets dropped by kernel
将数据保存为 pcapng 格式使用 tcpdump 或 Wireshark 进行分析
保存为 pcapng 格式
可以通过 -w 参数将抓包数据保存为 pcapng 格式:
[root@localhost tmp]# ./ptcpdump -i any icmp -v -w ping.pcapng
2024-08-13 09:57:33 WARN skip Docker Engine integration due to Cannot connect to the Docker daemon at unix:///var/run/docker.sock. Is the docker daemon running?
2024-08-13 09:57:34 WARN skip attach cgroup due to get cgroup v2 root dir failed: cgroupv2 is not mounted
2024-08-13 09:57:34 WARN the kernel does not support netfilter based NAT feature, skip attach kprobe/nf_nat_packet
2024-08-13 09:57:34 WARN the kernel does not support netfilter based NAT feature, skip attach kprobe/nf_nat_manip_pkt
2024-08-13 09:57:34 WARN ptcpdump: capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
^C
18 packets captured
18 packets received by filter
0 packets dropped by kernel
使用 Wireshark 进行分析
当使用 Wireshark 打开保存的 pcapng 格式的文件时,将在 Wireshark 的界面中显示相关的进程、容器以及 Pod 信息:
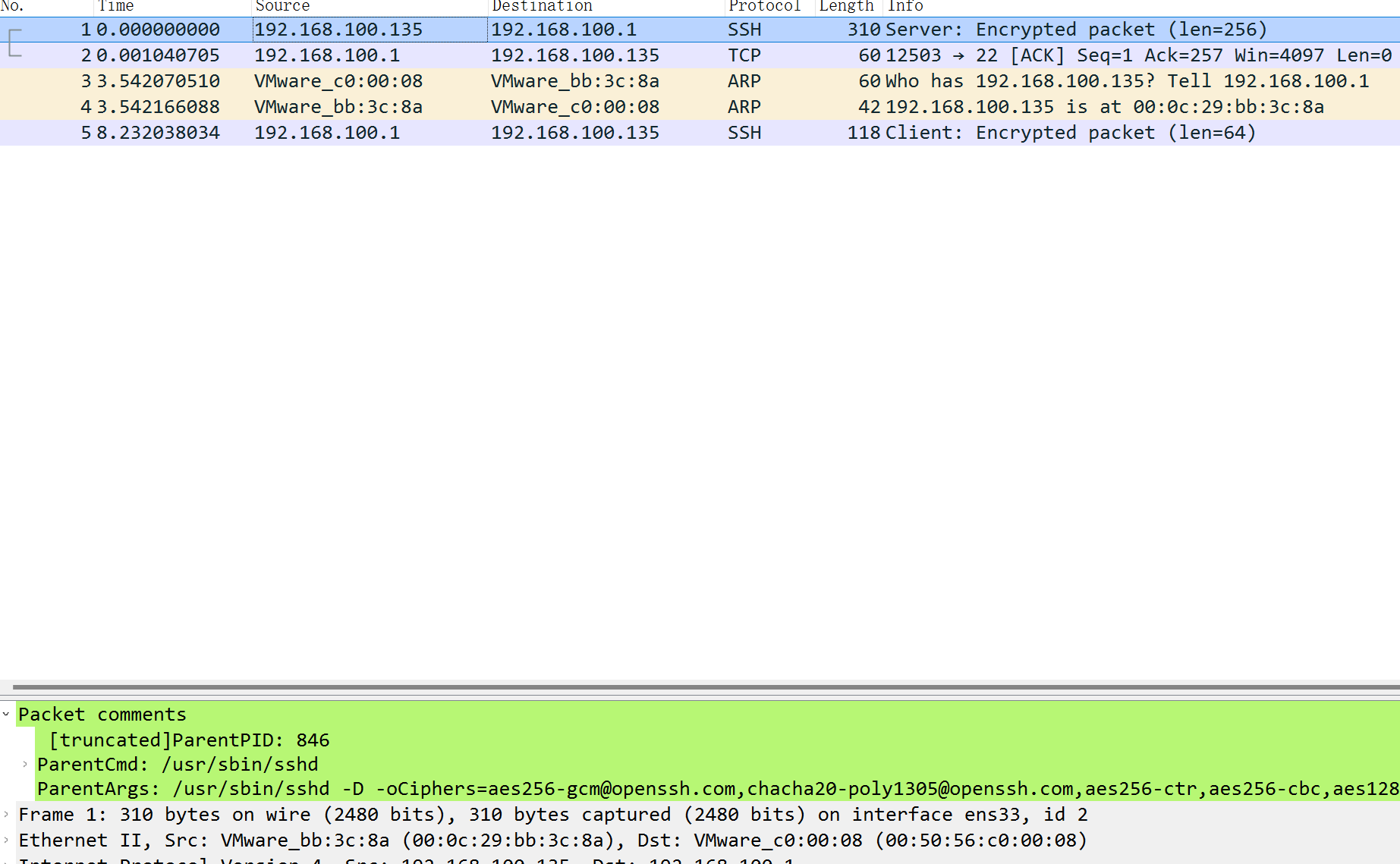
与 tcpdump 比较
| 选项 | tcpdump | ptcpdump |
|---|---|---|
| 表达 | ✅ | ✅ |
| -i 接口, –interface=接口 | ✅ | ✅ |
| -w x.pcapng | ✅ | ✅ (附进程信息) |
| -w x.pcap | ✅ | ✅ (不含进程信息) |
| -w– | ✅ | |
| -r x.pcapng, -r x.pcap | ✅ | ✅ |
| -r– | ✅ | |
| –PID process_id | ✅ | |
| –pname process_name | ✅ | |
| -f, –follow-forks | ✅ | |
| –打印 | ✅ | ✅ |
| -c 计数 | ✅ | ✅ |
| -Q 方向, –direction=方向 | ✅ | ✅ |
| –list-interfaces | ✅ | ✅ |
| -一个 | ✅ | |
| -B bufer_size, –buffer-size=buffer_size | ✅ | |
| –计数 | ✅ | |
| -C *file_size | ✅ | |
| -d | ✅ | |
| -dd | ✅ | |
| -ddd | ✅ | |
| -D | ✅ | |
| -e | ✅ | |
| -f | ✅ | ⛔ |
| -F 文件 | ✅ | |
| -G rotate_seconds | ✅ | |
| -h | ✅ | ✅ |
| –帮助 | ✅ | ✅ |
| –版本 | ✅ | ✅ |
| -H | ✅ | |
| -l, –monitor-mode | ✅ | |
| –即时模式 | ✅ | |
| -j tstamp_type, –time-stamp-type=tstamp_type | ✅ | |
| -J, –list-time-stamp-types | ✅ | |
| –time-stamp-precision=tstamp_precision | ✅ | |
| –微 | ✅ | |
| –纳米 | ✅ | |
| -K, –don’t-verify-checksums | ✅ | |
| -l | ✅ | |
| -L, –list-data-link-types | ✅ | |
| -m 模块 | ✅ | |
| -M 秘密 | ✅ | |
| -n | ✅ | |
| -N | ✅ | |
| -# | ✅ | ⛔ |
| –数 | ✅ | |
| -O, –no-optimize | ✅ | |
| -p, –无混杂模式 | ✅ | ⛔ |
| -S, –绝对 tcp-序列号 | ✅ | |
| -s snaplen, –snapshot-length=快照 | ✅ | |
| -T型 | ✅ | |
| -吨 | ✅ | |
| -tt | ✅ | |
| -TTT | ✅ | |
| -tttt | ✅ | |
| -u | ✅ | |
| -U, –packet-buffered | ✅ | |
| -v | ✅ | |
| -节 | ✅ | |
| -vvv | ✅ | |
| -V 文件 | ✅ | |
| -W filecont | ✅ | |
| -x | ✅ | |
| -xx | ✅ | |
| -X | ✅ | |
| -XX | ✅ | |
| -y datalinktype, –linktype=datalinktype | ✅ | |
| -z postrotate-命令 | ✅ | |
| -Z 用户,–relinquish-privileges=用户 | ✅ |
参考
1.https://mozillazg.com/2024/07/ebpf-ptcpdump-capturing-the-network-traffic-of-a-process-or-container-or-pod.html
2.https://github.com/mozillazg/ptcpdump