本文最后更新于 475 天前,其中的信息可能已经有所发展或是发生改变。
RabbitMQ开启SSL与SpringBoot连接测试
最近有一个需求,需要RabbitMQ开启ssl连接进行消费,之前因为生产也是直接内网部署,因此没考虑过ssl加密访问,因此这又是我的一个小知识点(漠叔的语气)
配置 RabbitMQ 开启 SSL
前提是已经部署了RabbitMQ ,我这边是单机测试,https://199604.com/2323可以参考此文档进行部署单机。
下载证书生成器,方便咱们生成证书
地址:https://github.com/jiomer/CMF-AMQP-Configuration
下载上传解压~
unzip CMF-AMQP-Configuration-master.zip
cd CMF-AMQP-Configuration/ssl
#修改生成证书10年有效期
sed -i "s/valid=365/valid=3650/g" create_client_cert.sh
sed -i "s/valid=365/valid=3650/g" make_server_cert.sh
sed -i "s/valid=365/valid=3650/g" setup_ca.sh
sed -i "s/default_days = 365/default_days = 3650/g" openssl.cnf
sh setup_ca.sh rabbitmqca
#生成服务端证书,第一个参数是服务端证书前缀,第二个参数是密码。密码任意,在当前目录下生成server目录
sh make_server_cert.sh rabbitmq-server rabbitmqca-server-passwd
#sh make_server_cert.sh rabbitmq-server Gzeport@123
#生成客户端证书,第一个参数是客户端证书前缀,第二个参数是密码。密码任意,在当前目录下生成client目录
sh create_client_cert.sh rabbitmq-client rabbitmqca-client-passwd
sh create_client_cert.sh rabbitmq-client Gzeport@123
配置 RabbitMQ 服务端的证书如下:
ca/cacert.pem #CA证书
server/rabbitmq-server.cert.pem #服务端公钥
server/rabbitmq-server.key.pem #服务端私钥
使用 RabbitMQ 服务端公钥证书生成 JKS 证书
# -alias后为别称,-file后是服务端公钥位置,-keystore后是输出JSK证书位置,此处相对路径 mykeystore
keytool -import -alias rabbitmq-server \
-file server/rabbitmq-server.cert.pem \
-keystore mykeystore -storepass changeit
#输入y回车
配置 RabbitMQ 客户端的证书如下:
client/rabbitmq-client.keycert.p12 #PKCS12证书,包含客户端所需公私钥及中间证书
mykeystore #服务端JKS格式公钥
默认 RabbitMQ 配置目录在 /etc/rabbitmq,我们创建个证书目录存放服务端证书
mkdir -p /etc/rabbitmq/ssl
#复制服务端必要证书
cp ca/cacert.pem \
server/rabbitmq-server.cert.pem \
server/rabbitmq-server.key.pem /etc/rabbitmq/ssl/
修改 RabbitMQ 配置文件
修改 RabbitMQ 配置文件 /etc/rabbitmq/rabbitmq.config,此文件默认不存在,需要手动创建
%%Disable SSLv3.0 and TLSv1.0 support.
[
{ssl, [{versions, ['tlsv1.2', 'tlsv1.1']}]},
{rabbit, [
{tcp_listeners, [5672]},
{ssl_listeners, [5671]},
{ssl_options, [{cacertfile,"/etc/rabbitmq/ssl/ca/cacert.pem"},
{certfile,"/etc/rabbitmq/ssl/server/rabbit-server.cert.pem"},
{keyfile,"/etc/rabbitmq/ssl/server/rabbit-server.key.pem"},
{verify, verify_peer},
{ciphers, ["ECDHE-ECDSA-AES256-GCM-SHA384","ECDHE-RSA-AES256-GCM-SHA384",
"ECDHE-ECDSA-AES256-SHA384","ECDHE-RSA-AES256-SHA384", "ECDHE-ECDSA-DES-CBC3-SHA",
"ECDH-ECDSA-AES256-GCM-SHA384","ECDH-RSA-AES256-GCM-SHA384","ECDH-ECDSA-AES256-SHA384",
"ECDH-RSA-AES256-SHA384","DHE-DSS-AES256-GCM-SHA384","DHE-DSS-AES256-SHA256",
"AES256-GCM-SHA384","AES256-SHA256","ECDHE-ECDSA-AES128-GCM-SHA256",
"ECDHE-RSA-AES128-GCM-SHA256","ECDHE-ECDSA-AES128-SHA256","ECDHE-RSA-AES128-SHA256",
"ECDH-ECDSA-AES128-GCM-SHA256","ECDH-RSA-AES128-GCM-SHA256","ECDH-ECDSA-AES128-SHA256",
"ECDH-RSA-AES128-SHA256","DHE-DSS-AES128-GCM-SHA256","DHE-DSS-AES128-SHA256",
"AES128-GCM-SHA256","AES128-SHA256","ECDHE-ECDSA-AES256-SHA",
"ECDHE-RSA-AES256-SHA","DHE-DSS-AES256-SHA","ECDH-ECDSA-AES256-SHA",
"ECDH-RSA-AES256-SHA","AES256-SHA","ECDHE-ECDSA-AES128-SHA",
"ECDHE-RSA-AES128-SHA","DHE-DSS-AES128-SHA","ECDH-ECDSA-AES128-SHA",
"ECDH-RSA-AES128-SHA","AES128-SHA"]},
{honor_cipher_order, true},
{fail_if_no_peer_cert, true},
{versions, ['tlsv1.2', 'tlsv1.1']}
]},
{auth_mechanisms,['PLAIN', 'AMQPLAIN', 'EXTERNAL']}
]}
].
主要配置项说明:
ssl_listeners指定 SSL协议的端口号,官方文档5671ssl_optionsSSL 认证配置项cacertfileCA 证书位置certfile公钥证书位置keyfile密钥证书位置verifyverify_peer客户端与服务端互相发送证书verify_none禁用证书交换与校验fail_if_no_peer_certtrue不接受没证书的客户端连接false接受没证书的客户端连接ciphers加密器
启用ssl插件
#启用rabbitmq_auth_mechanism_ssl作为EXTERNAL认证机制的实现
rabbitmq-plugins enable rabbitmq_auth_mechanism_ssl
#查看启动结果
rabbitmq-plugins list
重启 RabbitMQ
systemctl restart rabbitmq-server
验证开启 SSL 是否成功
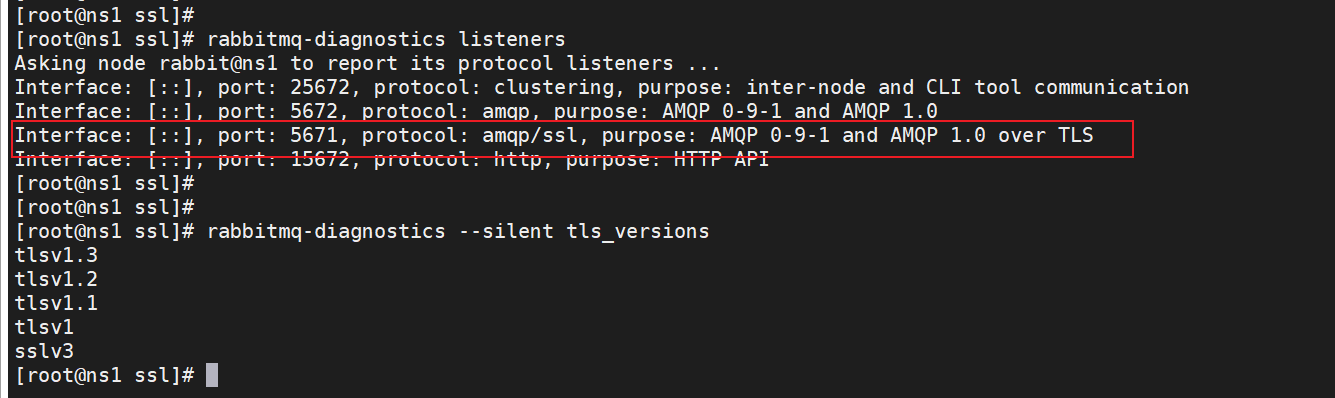
使用 Rabbitmq 自带的诊断工具查看端口监听状态及使用协议
#查看监听
rabbitmq-diagnostics listeners
#查看支持的TLS版本
rabbitmq-diagnostics --silent tls_versions
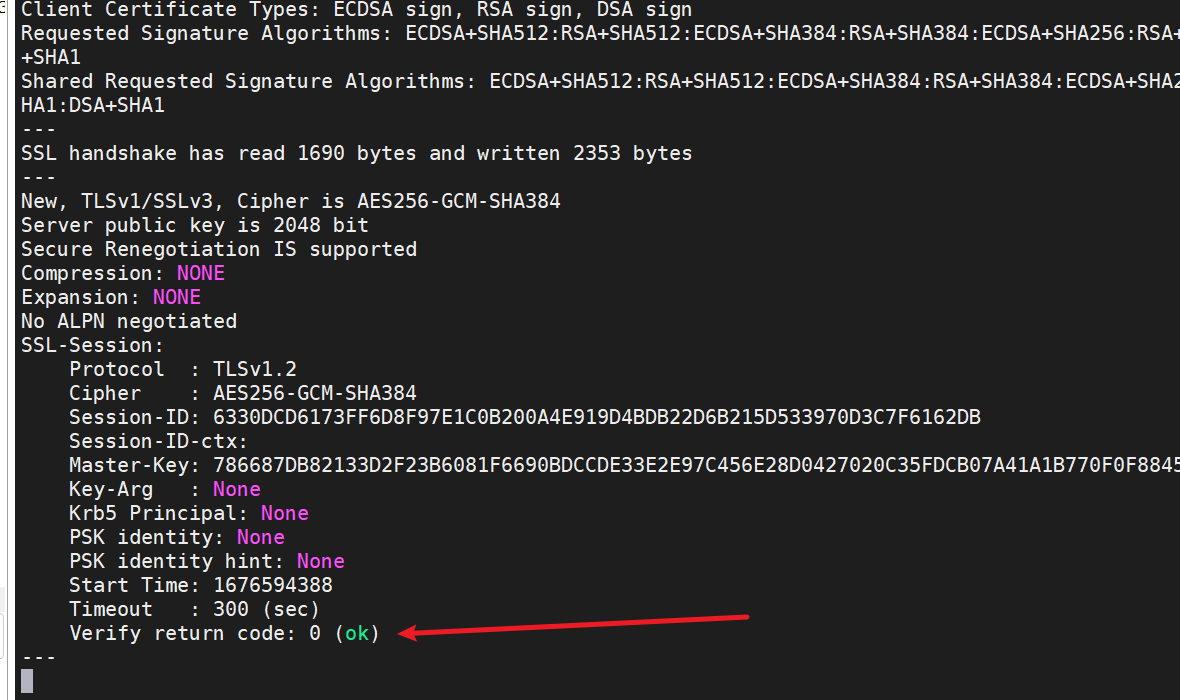
使用 OpenSSL CLI 工具验证证书是否有效
cd 生成证书的ssl目录
#使用客户端证书+CA证书连接RabbitMQ验证。本处MQ与生成证书是同一主机,其他情况请自行考虑。
openssl s_client -connect localhost:5671 \
-cert client/rabbitmq-client.cert.pem \
-key client/rabbitmq-client.key.pem \
-CAfile ca/cacert.pem
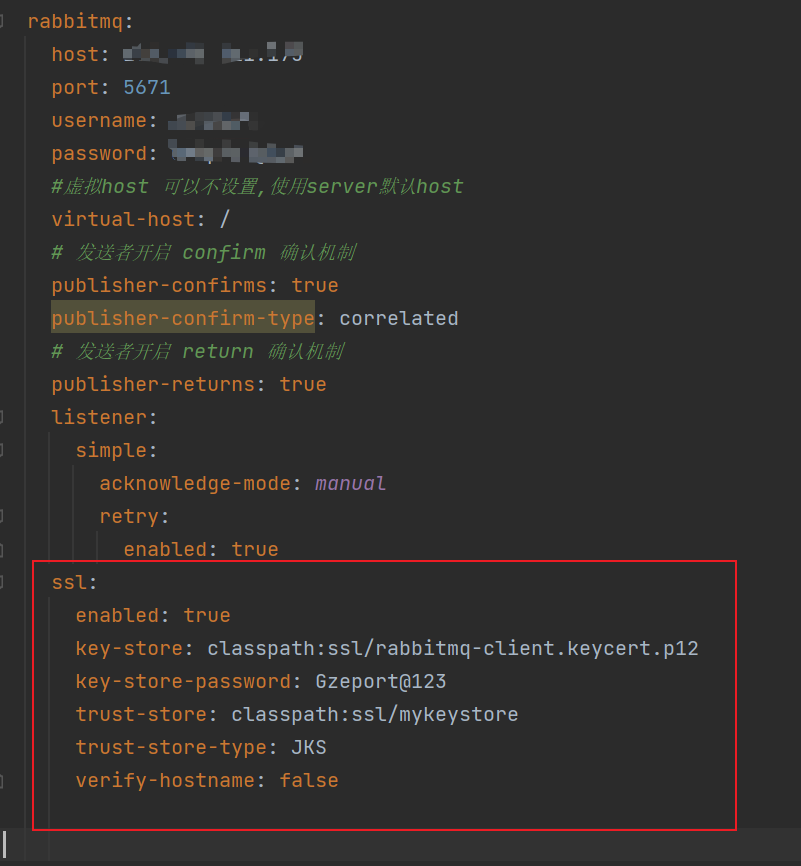
SpringBoot连接测试
配置文件 application.properties
剩下代码就是自己测试推送是否成功
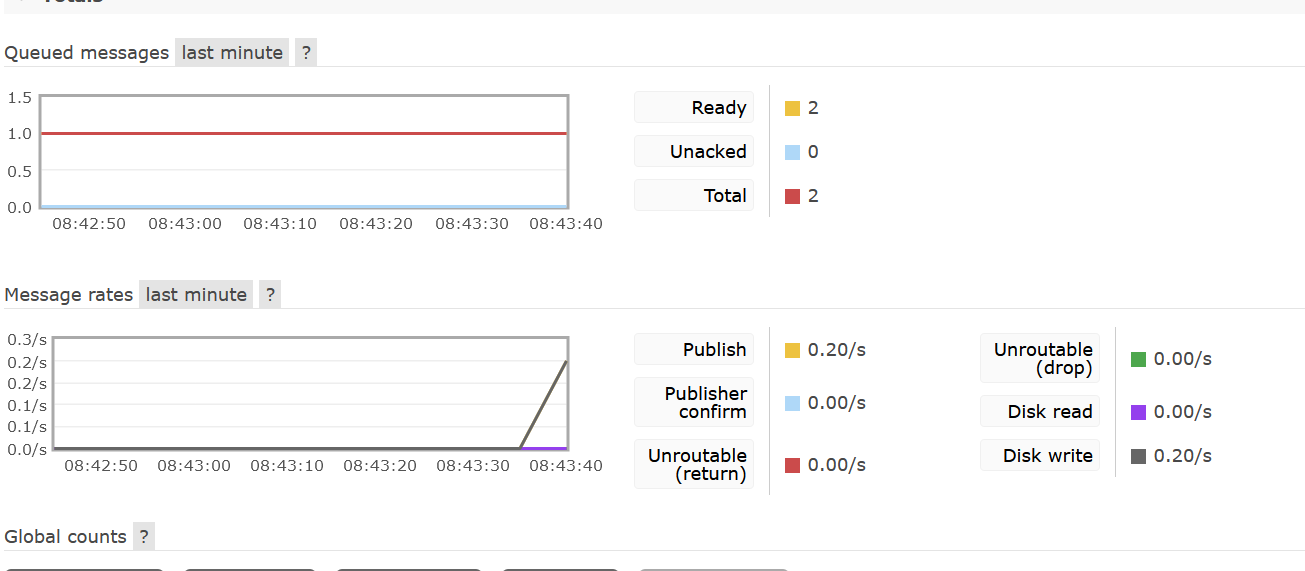
生产者推送消息成功,同理消费者也是配置上ssl相关信息即可。
参考:https://www.cnblogs.com/ybyn/p/13959135.html
https://www.cnblogs.com/hellxz/p/15776987.html
虽然看不懂,但看看总能了解一些。