CentOS7.9 部署Harbor2.x本地私有镜像仓库
一年前写过:harbor镜像仓库搭建配置,但是以1.x版本为基础得部署,此次是基于2.x的版本进行部署,在同步做一次部署过程的记录。
安装docker环境
省略,参考以往部署教程:Centos 安装Docker(含在线和离线)
安装docker-compose
省略,参考以往部署教程:Docker Compose学习手札
Harbor 安装:
Harbor 官方地址:https://github.com/goharbor/harbor/releases
本次安装版本为:v2.6.2
下载harbor软件包:
https://github.com/goharbor/harbor/releases/download/v2.6.2/harbor-offline-installer-v2.6.2.tgz
解压到指定的目录
tar xvf harbor-offline-installer-v2.6.2.tgz -C /data/docker/ && cd /data/docker/harbor/
修改harbor.yml配置文件
复制模板
mv harbor.yml.tmpl harbor.yml
修改了一下内容
hostname: hub.guoliangjun.com # 修改域名
# 关闭http访问方式
http:
# # port for http, default is 80. If https enabled, this port will redirect to https port
# port: 80
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /data/docker/harbor/cert/hub.guoliangjun.com.crt #取消注释,填写实际路径
private_key: /data/docker/harbor/cert/hub.guoliangjun.com.key #取消注释,填写实际路径
harbor_admin_password: Harbor12345 # admin用户登入密码
database:
password: root123 # 数据库密码
max_idle_conns: 100
max_open_conns: 900
# The default data volume
data_volume: /data/harbor #目录自己创建,根据实际情况填写
创建存放数据目录
mkdir /data/harbor
mkdir -p /data/docker/harbor/cert/
使用openssl创建自签证书并生成证书,并保存到/data/docker/harbor/cert/目录下
具体方法参考:https://goharbor.io/docs/2.6.0/install-config/configure-https/
创建CA
cd /data/docker/harbor/cert/
openssl genrsa -out ca.key 4096
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=DEVOPS/OU=DEVOPS/CN=hub.guoliangjun.com" \
-key ca.key \
-out ca.crt
创建证书请求文件csr
openssl genrsa -out yourdomain.com.key 4096
openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=DEVOPS/OU=DEVOPS/CN=hub.guoliangjun.com" \
-key hub.guoliangjun.com.key \
-out hub.guoliangjun.com.csr
创建证书
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=hub.guoliangjun.com
EOF
openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in hub.guoliangjun.com.csr \
-out hub.guoliangjun.com.crt
查看证书
[root@localhost harbor]# cd /data/docker/harbor/cert/
[root@localhost cert]# ls -l
总用量 28
-rw-r--r-- 1 root root 2041 12月 14 22:32 ca.crt
-rw-r--r-- 1 root root 3243 12月 14 22:32 ca.key
-rw-r--r-- 1 root root 17 12月 14 22:32 ca.srl
-rw-r--r-- 1 root root 2082 12月 14 22:32 hub.guoliangjun.com.crt
-rw-r--r-- 1 root root 1712 12月 14 22:30 hub.guoliangjun.com.csr
-rw-r--r-- 1 root root 3243 12月 14 22:29 hub.guoliangjun.com.key
-rw-r--r-- 1 root root 238 12月 14 22:31 v3.ext
启动harbor服务
cd /data/docker/harbor/
sh ./prepare
sh ./install.sh
添加本地域名解析访问
目录位置C:\Windows\System32\drivers\etc\hosts
新增192.168.100.146 hub.guoliangjun.com的解析记录
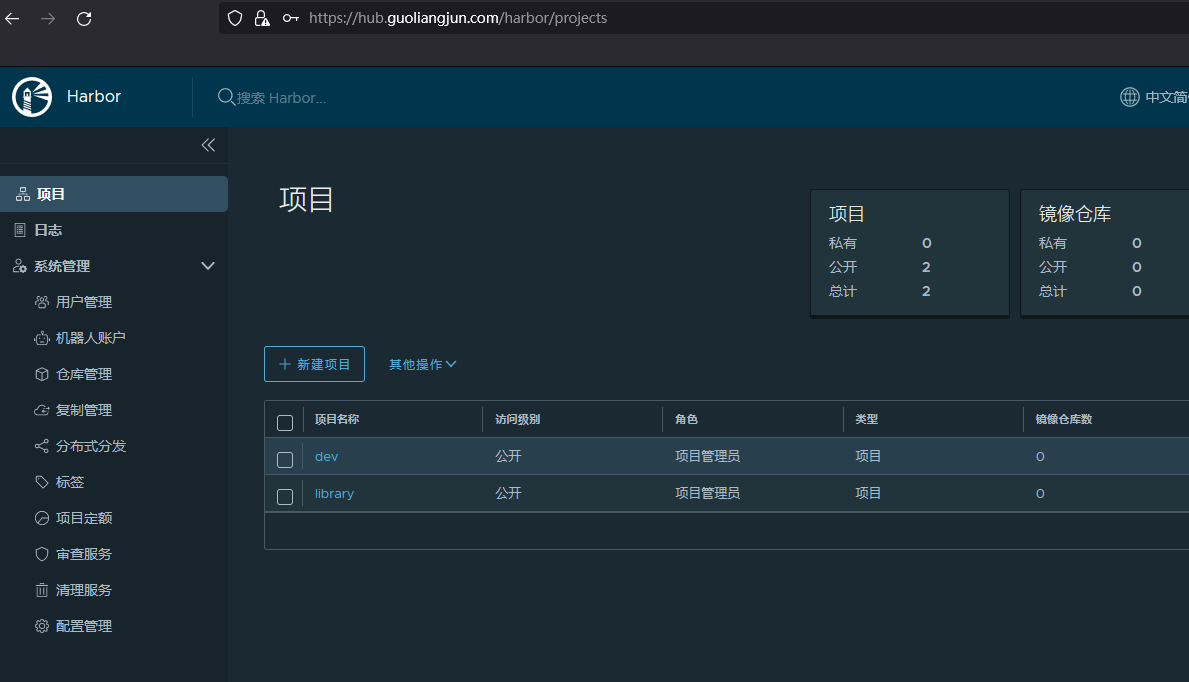
测试访问
https://hub.guoliangjun.comorhttps://192.168.100.146/
用户名:admin 密码:Harbor12345
添加docker仓库地址
echo "192.168.100.146 hub.guoliangjun.com" >> /etc/hosts
在/etc/docker/daemon.json新增"insecure-registries": ["https://hub.guoliangjun.com"]
重启docker服务:systemctl daemon-reload && systemctl restart docker && systemctl status docker
方法二放到/etc/docker/certs.d/(建议使用这种)
具体方法参考:https://goharbor.io/docs/2.6.0/install-config/configure-https/ –>Provide the Certificates to Harbor and Docker
需要将harbor服务端生成的CA证书拷贝到每个远程客户机的"/etc/docker/certs.d/harbor服务器的域名或ip/"目录下,如:
[root@localhost hub.guoliangjun.com]# pwd
/etc/docker/certs.d/hub.guoliangjun.com
[root@localhost hub.guoliangjun.com]#
[root@localhost hub.guoliangjun.com]# ls -l
总用量 4
-rw-r--r-- 1 root root 2041 12月 14 22:36 ca.crt
重启docker服务:systemctl daemon-reload && systemctl restart docker && systemctl status docker
登入地址
详细登入方式:docker login -u 用户 -p 密码 服务器IP:端口
[root@localhost docker]# docker login -u admin -p Harbor12345 https://hub.guoliangjun.com
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
重启harbor服务
cd /data/docker/harbor/
docker-compose stop
systemctl stop docker
systemctl daemon-reload
systemctl start docker
docker-compose start